
On May 4th, the National Computer Virus Emergency Response Center (China) website released a report titled “Investigation into ‘The Matrix’ – Central Intelligence Agency (CIA) of the United States (Part 1)”, revealing that the CIA has been secretly implementing “peaceful evolution” and “color revolutions” around the world for a long time, continuing to engage in espionage activities. The report suggests that the United States itself is a “Matrix”. The following is a detailed summary of the report:
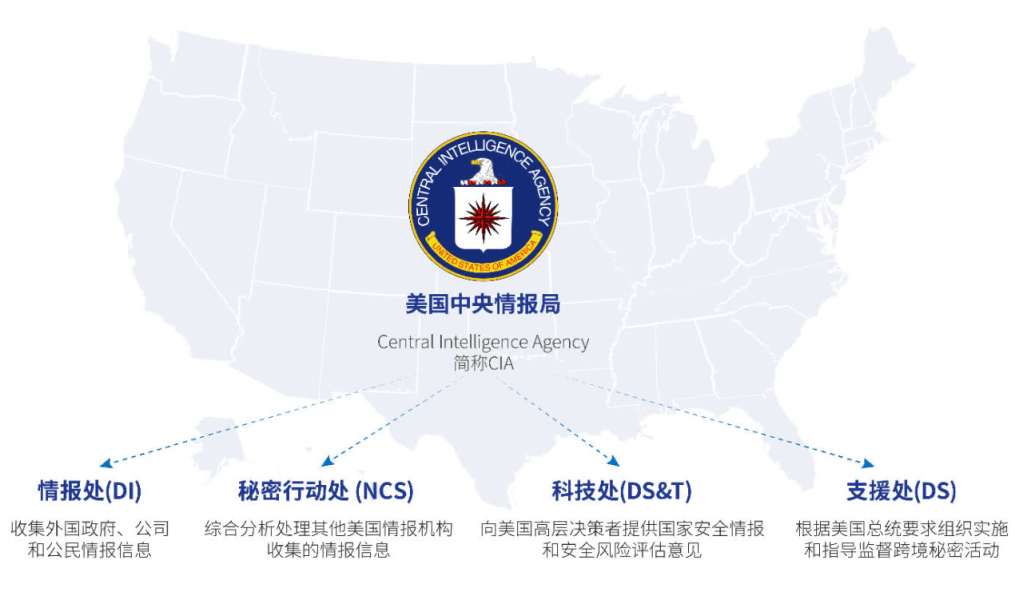
The Central Intelligence Agency (CIA), a name more well-known to the public than the National Security Agency (NSA) in the United States, is one of the main intelligence agencies of the federal government. Its headquarters is located in Langley, Virginia and it has four departments: the Directorate of Intelligence (DI), the National Clandestine Service (NCS), the Directorate of Science and Technology (DS&T), and the Directorate of Support (DS). Its main business scope involves collecting information on foreign governments, companies, and citizens, integrating and analyzing intelligence information collected by other U.S. intelligence agencies, providing national security intelligence and risk assessments to senior U.S. decision-makers, and organizing and directing cross-border clandestine operations in accordance with the requirements of the U.S. President.
For a long time, the CIA has been secretly implementing “peaceful evolution” and “color revolutions” around the world, continuing to engage in espionage activities.
Since the beginning of the 21st century, the rapid development of the Internet has provided the CIA with new opportunities for infiltration, subversion, and sabotage activities. Institutions and individuals around the world using American Internet equipment and software products have become the CIA’s puppet “agents,” helping the agency quickly become a shining “star” in the network intelligence war.
This series of reports starts with a large number of real cases investigated by the National Computer Virus Emergency Response Center and 360 company, revealing the main details of its network attack weapons, and disclosing the specific processes of typical network security incidents that have occurred in China and other countries. It comprehensively and deeply analyzes the CIA’s network attack espionage and related real-world harmful activities, as well as its contributions to making the United States a “Matrix”. The report provides references and advice for victims of network attacks around the world.
- Overview
From the impact on the international socialist camp in the 1980s, the Velvet Revolution in the early 1990s, the “Rose Revolution” in Georgia in 2003, the “Orange Revolution ” in Ukraine in 2004, the “Tulip Revolution” in Kyrgyzstan in 2005, the “Arab Spring” in North Africa and Western Asia in 2011, to the “Second Color Revolution” in Ukraine and the “Sunflower Movement ” in Taiwan in 2014, all have been recognized by international organizations and scholars around the world as typical cases of “color revolutions” led by US intelligence agencies. Other countries have also experienced attempted “color revolutions,” such as the “Snow Revolution” in Belarus in March 2005, the “Orange Storm” in Azerbaijan in June 2005, the “Cedar Revolution ” in Lebanon in 2005, the “Saffron Revolution” in Myanmar in 2007, and the “Green Revolution” in Iran in 2009. If we count from the Cold War era, there are countless regime change events with the color of “peaceful evolution” and “color revolution.” According to statistics, the CIA has overthrown or attempted to overthrow at least 50 legal governments in other countries over the past few decades (while only recognizing seven), causing unrest in those countries.
In analyzing the various technical, information communication, and on-site command factors in these events, it can be seen that they are critical to their success or failure. The United States is in a leading position in these technologies, especially after pushing the Internet to the international stage in the 1980s, which was widely accepted by countries around the world. This provided unprecedented technological possibilities for US intelligence agencies to launch “color revolutions” abroad.
Former US Secretary of State Albright once boasted, “With the Internet, we have a way to deal with China.” This statement is not unfounded, as many “color revolutions” have seen the shadow of Western powers using the Internet to push the agenda. After the “Arab Spring” in many countries in Western Asia and North Africa, some large multinational Internet companies in the US actively intervened, investing heavily in manpower, material resources, and financial resources, wooing support for opposition forces, openly criticizing legal governments that were not in line with US interests, assisting in the dissemination of false information, and promoting the continuous escalation of protest activities.
- Providing encrypted network communication services. To help protesters in some countries in the Middle East maintain smooth communication while avoiding tracking and arrest, US companies (allegedly with US military backgrounds) developed a TOR technology (The Onion Router) that can access the international Internet and cannot be traced. Relevant servers encrypt all information passing through them, thereby helping specific users to surf the Internet anonymously. After the project was launched by US companies, it was immediately provided free of charge to anti-government personnel in countries such as Iran, Tunisia, and Egypt, ensuring that those “dissenting young people who want to shake the ruling of their own government” can avoid local government censorship and surveillance while participating in activities.
- Providing network communication services in the event of a network interruption. To ensure that anti-government personnel in countries like Tunisia and Egypt can still communicate with the outside world in the event of a network interruption, US companies such as Google and Twitter quickly launched a dedicated service called “Speak2Tweet,” which allows users to dial in and upload voice messages for free. These messages are automatically converted into tweets and then uploaded to the Internet, which platforms such as Twitter publicly release, completing real-time reporting on the scene of the events.
- Providing on-site command tools for rallies and marches based on the Internet and wireless communication. The US RAND Corporation spent several years developing a non-traditional regime change technology called “swarming,” which was used to help a large number of young people connected through the Internet join the mobile protest activities of “shoot one place and move to another,” greatly improving the efficiency of on-site command during these activities.
- The development of the “Riot” software by US companies, which supports 100% independent wireless broadband networks and provides variable WiFi networks, not relying on any traditional physical access methods, without the need for phone, cable, or satellite connections, and can easily evade any form of government surveillance. With the powerful network and communication technology mentioned above, the US CIA has planned and organized a large number of “color revolutions” events around the world.
- The US State Department considers the development of “anti-censorship” information systems as an important task and has allocated more than 30 million US dollars to the project.

2. The CIA’s series of cyber weapons
On March 7, 2017, the WikiLeaks website disclosed 8,716 secret documents allegedly from the CIA’s Center for Cyber Intelligence, involving the hacking techniques of the CIA’s hacking team, code names for attack operations, technical specifications and requirements for attack tools, etc. WikiLeaks referred to the related documents as “Vault 7,” which caused widespread attention worldwide.
In 2020, 360 Security Technology independently discovered an APT organization that had never been exposed to the outside world. It specializes in carrying out network attacks and theft activities against China and its friendly countries. The victims are scattered all over the world. We have separately numbered it as APT-C-39. There is evidence that the organization uses network weapon tools related to “Vault 7” data (including Athena, Fluxwire, Grasshopper, AfterMidnight, HIVE, ChimayRed, etc.) to carry out network attacks against Chinese and other countries’ targets. The attack activity can be traced back to as early as 2011, and the relevant attacks have continued to this day. The targeted victims involve many aspects of various countries’ important information infrastructure, aviation and aerospace, research institutions, petroleum and petrochemical, large Internet companies, and government agencies.
In a large-scale global cyberattack operation, the CIA extensively uses “zero-day” (0day) vulnerabilities, including a large number of undisclosed backdoors and vulnerabilities (some of which have been verified), to establish “zombie” networks and attack proxy networks around the world, targeting network servers, network terminals, switches, and routers, as well as a large number of industrial control devices in stages. In the discovered network attack operations specifically targeting targets within China, we have successfully extracted multiple samples of “Vault 7” cyber weapons. Several Southeast Asian and European partners have also extracted almost identical samples, including:
2.1 Fluxwire backdoor program platform
A complex backdoor attack management platform that supports nine mainstream operating systems such as Windows, Unix, Linux, MacOS, and six different network architectures. It can form a fully autonomous mesh network with many “zombie” nodes, supporting self-repair, cyclic attacks, and multi-path routing.
2.2 Athena program
A lightweight backdoor program targeting Microsoft Windows operating systems, developed by the CIA in collaboration with Siege Technologies (acquired by Nehemiah Security in 2016). It can be implanted through remote installation, supply chain attacks, man-in-the-middle attacks, and physical contact installation, and it resides in the form of Microsoft Windows services. All attack function modules are decrypted and executed in memory in the form of plug-ins.
2.3 Grasshopper Backdoor Program
A sophisticated and configurable backdoor program targeting the Microsoft Windows operating system, capable of generating malicious payloads in various file formats (EXE, DLL, SYS, PIC). It supports multiple execution methods and can remain hidden and execute spy functions when combined with different plugin modules.
2.4 AfterMidnight Backdoor Program
A lightweight backdoor program that runs as a Microsoft Windows operating system DLL service. It dynamically transmits and loads the “Gremlins” module via HTTPS protocol, and executes the malicious payload in an encrypted manner.
2.5 ChimayRed Exploit Tool
An exploit tool suite targeting MikroTik and other brand routers, which, when combined with exploits, can implant lightweight network device backdoors such as “TinyShell.”
2.6 HIVE Network Attack Platform
The “HIVE” network attack platform is jointly developed by a subsidiary of the US Central Intelligence Agency (CIA) and a well-known US military industrial enterprise, Northrop Grumman (NOC). It provides a structurally complex method for the CIA’s network attack team to conduct continuous attacks and theft. It manages and utilizes a large number of compromised assets worldwide, forms multi-layer dynamic jump stations and secret data transmission channels, and uploads user accounts, passwords, and privacy data to the CIA 24/7 (https://www.cverc.org.cn/head/zhaiyao/news20220419-hive.htm).
2.7 Other Derived Tools
During the implementation of attacks and thefts using the “Vault7” network weapons mentioned above, the US Central Intelligence Agency (CIA) also derived and used a large number of attack samples beyond the “Vault7” data. Extracted samples include disguised phishing software installation packages, keyboard logging components, system information collection components, USB file theft modules, and various open-source hacker tools.
- Function Analysis of US Central Intelligence Agency (CIA) Network Attack Weapon Samples
In the investigation of multiple typical network attack incidents in China, 360 Company captured and successfully extracted a large number of Trojan programs, functional plugins, and attack platform samples closely related to the “Vault7” data exposed on the network from the victim’s information network. In-depth analysis found that most of the relevant program samples followed the malicious software development standards and technical specifications of the US Central Intelligence Agency (CIA), such as the “Network Operations Division In-memory Code Execution Specification,” “Network Operations Division Cryptographic Requirements,” and “Network Operations Division Persisted DLL Specification” in the “Vault7” data. These standards and specifications correspond to the loading and execution of malicious code, data encryption, and persistence behavior in network attack and theft activities. The relevant network weapons have undergone extremely strict standardized, process-oriented, and professional software engineering management. It is reported that only the US Central Intelligence Agency (CIA) strictly adheres to these standards and specifications for developing network attack weapons.
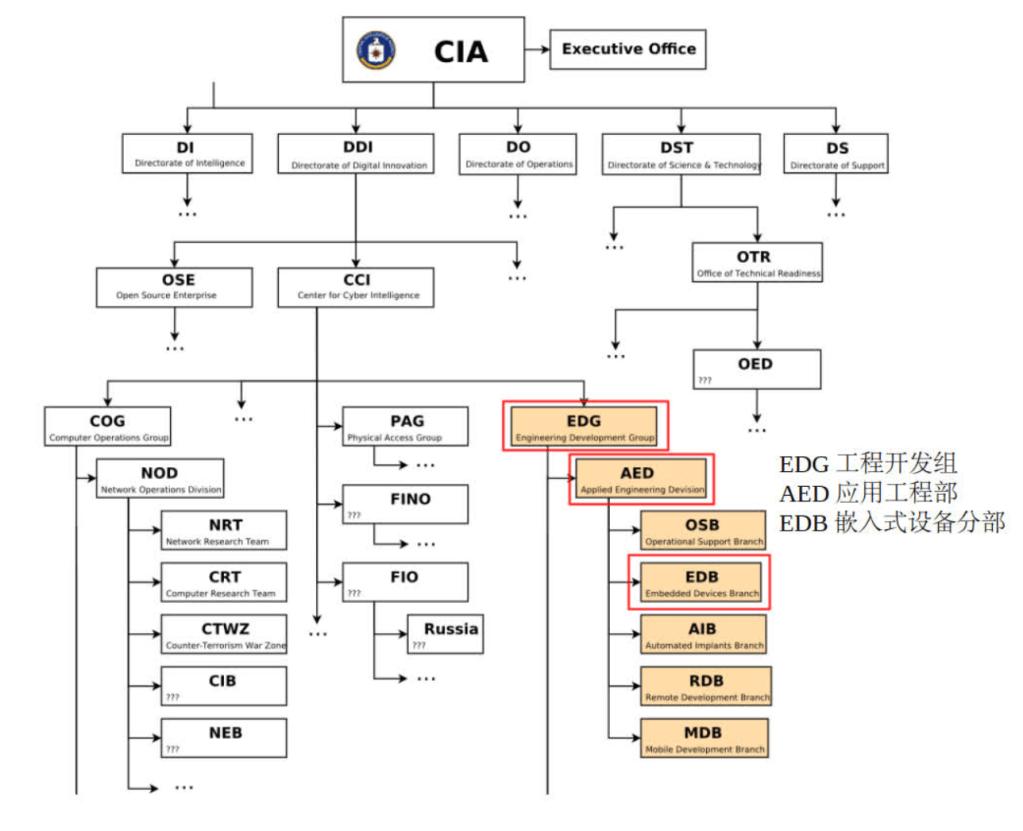
According to the “Vault7” data, the above-mentioned network attack weapons belong to the Engineering Development Group (EDG) of the US Central Intelligence Agency (CIA), and are independently or jointly developed by multiple branches under it, including the Applied Engineering Department (AED) and the Embedded Devices Branch (EDB). Most of these network weapons were born in a highly confidential internal network of the CIA called “devlan.net.” “Devlan.net” is a massive network weapon development and testing infrastructure established by the Engineering Development Group (EDG) of the CIA. According to the development log data of “devlan.net,” at least 200 engineers from the EDG were involved in the development of only the “HIVE” project.
Further technical analysis revealed that the backdoor programs and attack components of the US Central Intelligence Agency (CIA) mostly run in memory without physical files, making it extremely difficult to discover and collect evidence on related samples. Nevertheless, the joint technical team has successfully found effective methods to solve the difficulty of evidence collection. For convenience in describing and analyzing the issue, we temporarily classify the CIA’s attack weapons into 9 categories:
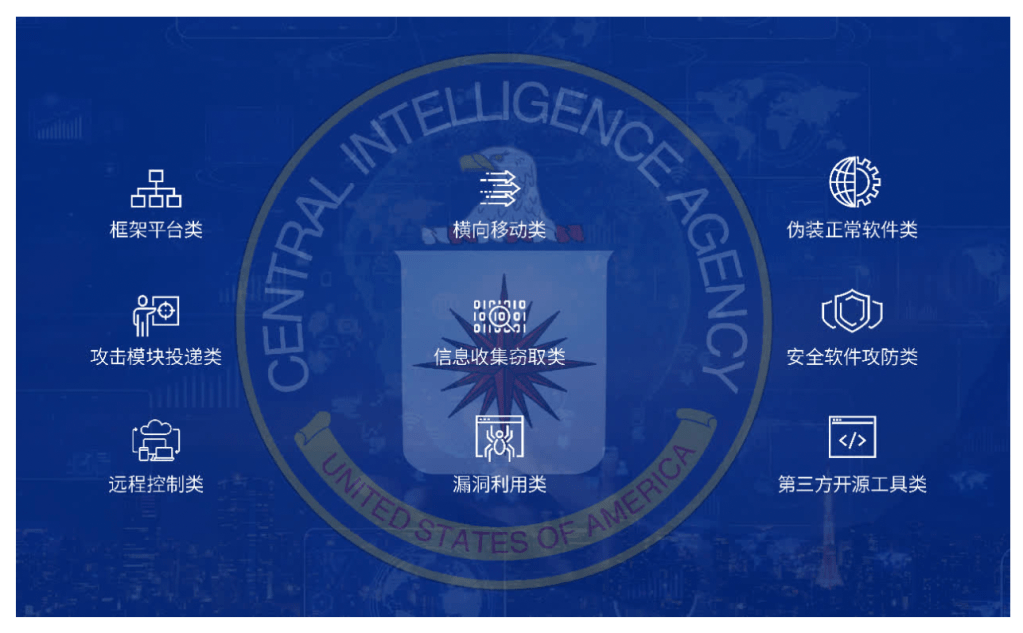
3.1 Framework platform category. We found and captured attack samples and activities of Fluxwire, Grasshopper, and Athena. Through field testing, the functionality, attack characteristics, and network behavior of these samples can confirm the descriptions in the “Vault7” data one by one.
3.2 Attack module delivery category. The CIA used a large number of simple malicious code downloaders to load and execute more malicious code and modules. The related samples have no special malicious functions and features, but when cooperating with framework platforms and other attack weapons, they can demonstrate powerful espionage capabilities, making it extremely difficult to attribute and trace them.
3.3 Remote control category. Multiple remote control plugins have been extracted, most of which are attack module components derived from framework platform attack weapons, and the two cooperate with each other.
3.4 Lateral movement category. A large number of malicious program samples extracted include backdoor programs implanted through Windows remote services using administrator credentials. In addition, the CIA also hijacked the upgrade program of various security products on the internal network, issued and installed backdoor programs through the internal network upgrade server’s upgrade function, and implemented lateral movement attacks in the internal network.
3.5 Information collection and theft category. The joint technical team accidentally extracted an information stealing tool used by the CIA, which belongs to one of the 48 advanced network weapons in the leaked classified document “ANT catalog” of the US National Security Agency (NSA), and is a dedicated information stealing tool of the NSA. This situation indicates that the CIA and the NSA may jointly attack the same target, share network attack weapons, or provide relevant technical or manpower support to each other. This adds new important evidence for attributing and tracing the identity of APT-C-39 attackers.
3.6 Vulnerability exploitation category. It was found in the investigation that since at least 2015, the CIA has established a huge network attack proxy resource all over the world, using “zero-day” vulnerabilities to indiscriminately attack IoT devices and network servers globally, and converting a large number of compromised devices into proxy “zombies,” hiding their own attack behavior, or blaming other countries for network attacks. For example, the CIA used a vulnerability attack suite code-named “ChimayRed” to target multiple models of MikroTik brand routers, including a large number of network devices using these routers in China. During the attack, the CIA would first maliciously modify the router’s startup script to continue executing the backdoor program after the router restarts; then, the CIA would modify the router’s CGI program to block the vulnerabilities that the CIA itself used to prevent other attackers from invading and causing privilege loss; finally, the CIA would implant exclusive backdoor programs such as “HIVE” or “TinyShell” into the router that only the CIA could use.
3.7 Disguised normal software category. The CIA customizes backdoor programs to disguise them as less popular software installation packages used by the target, and implements precise social engineering attacks against the target’s network environment.
3.8 Security Software Attack and Defense: The CIA has acquired attack tools specifically designed to attack commercial antivirus software. These tools can remotely shut down and kill the processes of specified antivirus software, rendering them ineffective against CIA cyberattacks or weapons.
3.9 Third-Party Open-Source Tools: The CIA also frequently uses ready-made open-source hacker tools for their attack activities. Their initial attacks target the victim’s network devices or servers and may also involve social engineering. Once they gain access, they further explore the target organization’s network topology, move laterally within the internal network, and steal more sensitive information and data. Computers controlled by the CIA are monitored 24/7, and all keystrokes are recorded, clipboard copy-paste information is stolen, and the insertion status of USB devices (primarily external hard drives and flash drives) is monitored in real-time. Once a USB device is plugged in, the victim’s private files on the USB device are automatically stolen. When conditions permit, the camera, microphone, and GPS location devices on the user’s terminal are also remotely controlled and accessed.
- Summary
The US-controlled cyber hegemony began in cyberspace, covering the world and affecting the globe. As one of the three major intelligence-gathering agencies in the United States, the CIA has already shown characteristics of automation, systematization, and intelligence in its global cyber attacks. In just the 8,716 leaked documents on the WikiLeaks website, many important hacker tools and cyber attack weapons of the US intelligence department were revealed, indicating that the US has built the world’s largest cyber weapon arsenal. Through empirical analysis, we found that their cyber weapons use extremely strict spy technology standards, with various attack methods interlocking and covering almost all Internet and IoT assets worldwide, allowing them to control other countries’ networks and steal important, sensitive data at any time and anywhere. This undoubtedly requires a large amount of financial, technical, and human resources support, and the American-style cyber hegemony is evident. “The Empire of Hackers” is well-deserved.
This report series attempts to disclose the various activities of the CIA’s long-term cyber attacks and espionage targeting Chinese network targets and to explore these cyber attacks and data theft activities.
In response to the highly systemic, intelligent, and concealed cyber attacks launched by the CIA against China, it is particularly important for domestic government agencies, research institutions, industrial enterprises, and commercial organizations to quickly “see” and take “action” in the first place. To effectively cope with the imminent threat of cyber and real-world threats, we should quickly organize and carry out self-inspection and self-examination of APT attacks while using domestically produced equipment with independent controllability. We should gradually establish a long-term defense system to achieve comprehensive and systematic prevention and control, resisting advanced threat attacks.
(Source: China National Computer Virus Emergency Response Center)

Leave a comment